API
The Tabidoo API is a simple way to integrate your app with Tabidoo. If you're a developer or familiar with APIs, you should be able to build a complete integration within minutes.
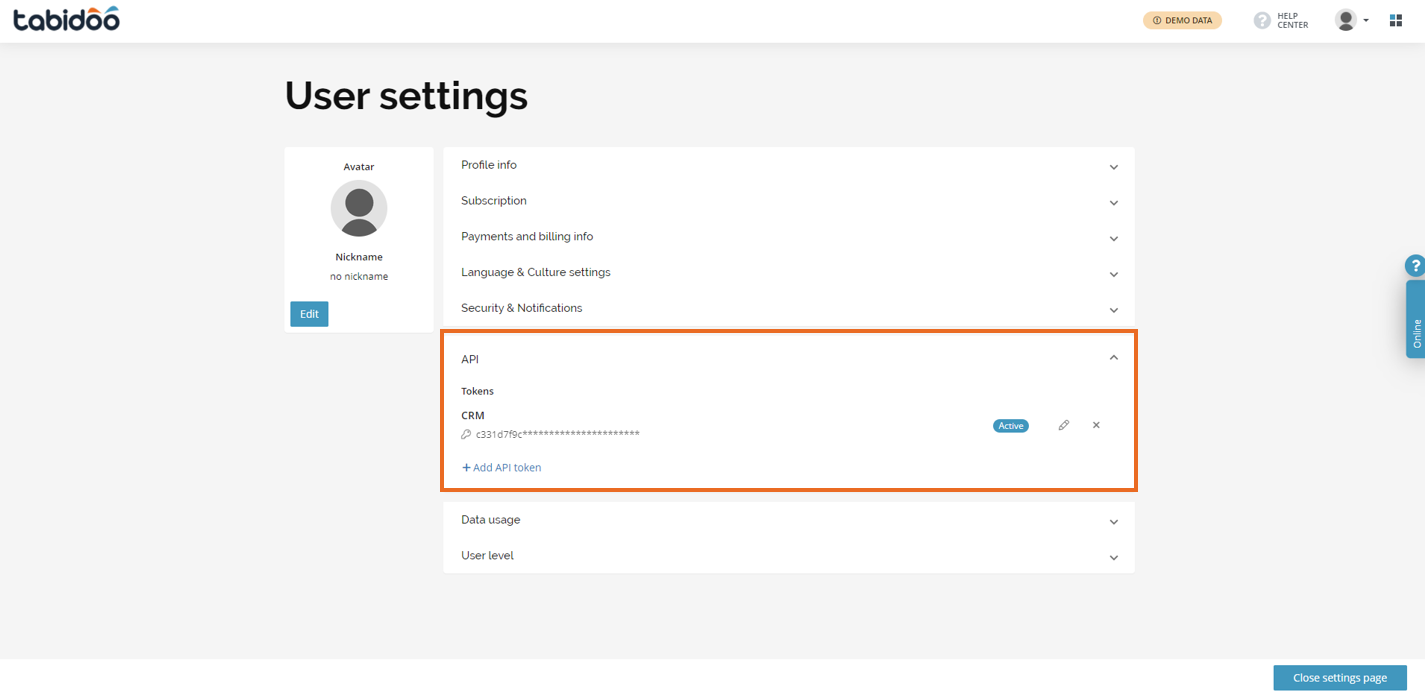
Where to find the API section in Tabidoo?
You can generate the API token in the user settings of your account.
Token Overview
1. Standard JWT Token
Usage: General API access for managing data, structure, users, etc.
Generated in: User Settings > API section
Access Level: Full access equivalent to the user's permissions
Security Note: Treat this token as your password—keep it secret and secure.
2. API Token with Assigned Role
Usage: Integration scenarios where controlled access is required
Management: Created by administrators and assigned a role with specific permissions
Best Practice: Use this token for automated tasks or integrations to limit risk exposure
3. Short API Token
Usage: Uploading files or images (e.g., attachments, avatars, public forms)
Lifespan: Short-term, lower privileges
Source: Generated per task, used in isolated upload actions
4. Public Form Tokens
Usage: Publicly accessible forms for external data collection
Behavior: Embedded in the public form URL; no login required
Security Consideration: Ensure form data is validated and usage restricted by design
5. Workflow Execution Tokens
Usage: Triggering workflow actions (e.g., via HTTP requests or external services)
Typical Scenario: Automated triggers from external systems
How to Use Tokens in API Calls
All API calls must include an Authorization header in the following format:
Authorization: Bearer <your-token>Example:
curl -X GET https://api.tabidoo.cloud/api/v2/table/data \
-H "Authorization: Bearer eyJhbGciOi..."Make sure to use HTTPS for all API interactions.
Token Usage in Workflow Automation
Tabidoo workflows can use tokens to fetch or submit data from/to external sources. Here’s where tokens often apply:
Load External Data: When importing from APIs, FTP, or shared drives, tokens authenticate access.
Trigger Workflow via API: A token is required to securely trigger execution of workflows externally.
Access Control: Tokens can dictate what level of access a workflow automation has.
Best Practices for Token Security
Use API tokens with limited roles for external integrations.
Store tokens securely (e.g., in environment variables).
Rotate tokens periodically.
Revoke tokens when no longer needed or if compromised.
Avoid exposing tokens in frontend code or public repositories.
Example Use Cases
| Use Case | Recommended Token |
|---|---|
| Public form submission | Standard API Token |
| Integration with external systems (Zapier, Make.com) | API Token with Role |
| Upload images or attachments | Short API Token |
| Internal admin scripting | Standard JWT Token |
| Trigger workflows from external webhook | Standard API Token |
Note: Improper token usage can lead to unauthorized access or data leaks. Follow the principle of least privilege and review permissions regularly.
Date and time handling in API
For more information about Date and time handling in API, visit "Date and time handling in workflow scripts, form scripts and API" chapter
For more information, visit Full API documentation.